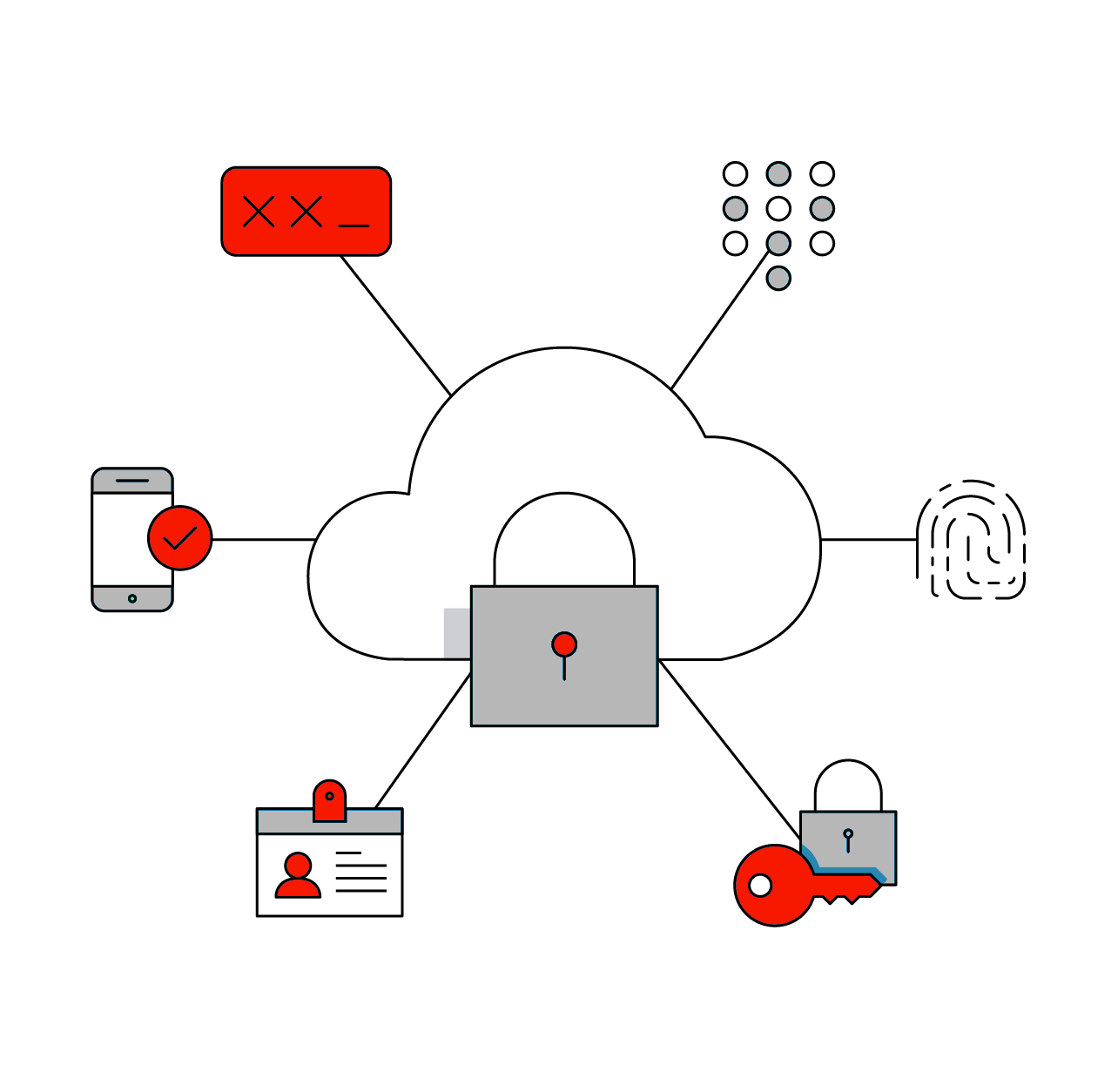
Identity and Access Management
Granting Access to Authorized Users While Prohibiting Unauthorized Ones
Identity and Access Management

Protecting your organization and reducing the incidence of identity-related risk means instituting a solid approach to identity governance. Core Security, a HelpSystems Company, helps you develop the strong identity governance foundation critical for the success of your identity and access management program. Our solutions are designed to improve transparency and add context to access relationships. They help you detect when inappropriate access is provisioned so you can resolve issues quickly. Not only do these identity governance capabilities enable you to increase security and comply with industry and government regulations, but they also help your team simplify their work with automated workflows and fast access to important assets.
Penetration testing offers many benefits, allowing you to:
- Allows users to reset passwords without involving the help desk.
- Enables users to unlock their own accounts.
- Permits self-enrollment of devices and tokens.
- Enables users to add their own information like telephone numbers, e-mail addresses, knowledge-based questions, answers, and more.
Enabling self-service reduces user friction and time, increases productivity and can significantly reduce help desk calls, a win-win for all.

Critical Self-Service Functionality
Enables users to address common issues all by themselves – password resets, account unlocking, self-enrollment (device and tokens), profile updates and more.

Integrated Component of a Comprehensive Identity Solution
Unlike most other single sign-on providers, Core Security offers user self-service as a fully integrated offering alongside other solutions.

Understanding the Cost Impact
Example: 5000 user organization with each user calling the Help Desk once a month for any or all of the reasons above = 60,000 calls. If 50% of those calls could be addressed with self-service = 30,000 calls affected. At a conservative estimate of $15/call = $450,000 savings.
Core Access Assurance Suite is an integrated identity and access management solution that delivers informed provisioning, continuous compliance, and actionable analytics. This solution is needed to streamline provisioning, automate the governance process, and be able to view advanced intelligence to discover hidden risks.
With Core Access Assurance Suite, you can apply predictive analytics to huge volumes of access-related data to reveal the complete context of relationships between user IDs, applications, and environments.

Self-Service Across Enterprise Systems
Rapid deployment policy and modular architecture get you up and running quickly, without a substantial investment in prerequisite systems.

Automate Processes for Managing User Accounts
Use fewer resources to manage and maintain the system over time, delivering lower total cost of ownership.

Protect Sensitive Data
Access request management system designed to simplify the process of creating and managing the requests that govern user access.
Certify User Access Rights
Certify user access rights effectively, while enforcing least privileged access across the enterprise. Strengthen compliance with corporate security policies, industry standards, and government regulations.
Penetration testing should be performed on a regular basis to ensure more consistent IT and network security management. A pen-tester will reveal how newly discovered threats or emerging vulnerabilities may potentially be assailed by attackers. In addition to regularly scheduled analysis and assessments required by regulatory mandates, tests should also be run whenever:
- New network infrastructure or applications are added
- Significant upgrades or modifications are applied to infrastructure or applications
- New office locations are established
- Security patches are applied
- End user policies are modified

Core Role Designer
A fully deployed Roles Based Access Control (RBAC) program promises to deliver improved compliance, more efficient provisioning, and increased security posture for your organization.

Core Certify
Stop rubber stamping your user access requests. See how a visualized, analytics-driven access review process results in a more effective and efficient review.



